Email - Display Name spoofing spam
N.B. This is written for a less-technical audience for a particular type of email spam that I am seeing a lot of lately. It’s not a comprehensive guide to everything email security related.
What is it?
Display Name Spoofing is a tactic that some spammers use to make their emails appear as if they’re coming from a legitimate source, such as a bank, a company you trust or a friend. Essentially, the spammers change the “From” field in the email to make it look like it’s coming from someone familiar.
This is done to trick people into opening the email as it looks like it’s from someone you know or someone important like your boss.
If you check the EMAIL ADDRESS, rather than the DISPLAY NAME then you will see it’s not their normal address, and likely a very dodgy looking one like in this example.
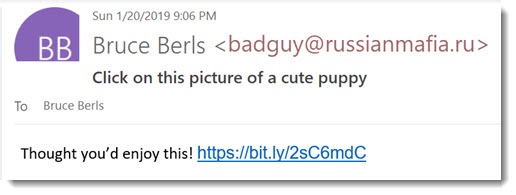
But sometimes it can look legitimate at first glance - @nationwde.co.uk for example? (Did you notice the missing i at first?)
Why does it get through?
Email isn’t very secure and whilst it’s possible to send an email from prime.minister @ no10.gov.uk email systems are very good nowadays at recognising this obvious spam.
But it’s not so easy with the Display Name - “The PM, prime.minister @ no10.gov.uk” will get blocked, but “The PM, r235 @ e323t.com” will likely get through to you as the email systems have no way of knowing that “The PM” is not a legitimate name for whomever uses the email address r235 @ e323t.com.
So why do they do this?
The first hurdle for SPAM email is to get you to open it. They hope that once the email appears in your inbox you will not notice the dodgy email address as it appears to come from someone you know like a friend or your boss.
It can be some annoying advert, a link or send you to a site with malware or a phishing attack (where it attempts to look like your bank so you put your password in).
In some carefully targeted cases scammers have spoofed an email appearing to come from a boss or CFO with instructions to urgently wire some £££ to a ‘suppliers’ account or similar.
How do they know who’s name to use?
Occasionally it’s targeted (like in the case of someone pretending to be your boss).
But the vast majority is automated high volume spam. They need a name that you recognise - this can be found through all sorts of ways like scraping Facebook or somewhere your name and email address appears alongside other. Websites are hacked all the time and this information is constantly leaked onto the internet. To scare yourself check out https://haveibeenpwned.com/
One very easy source is when group emails fall into the wrong hands. If there are 50 people cc’d, they now have over a thousand combinations of names and email addresses of people who know each other.
So does this mean the person who this email appears to come from has been hacked?
Not necessarily, in fact probably not.
In the above example where a group email to 50 people has fallen into the wrong hands then any one of those 50 people may have been hacked or the source of the leak. Whomever it is could still have a compromised password or PC, or it could have been fixed long ago but the info is already out there.
So who it appears to come from can’t stop it then?
They should ensure they have a secure password and an up-to-date PC of course, but after that no. If some crazy bloke comes up to you in a pub claiming to be Elon Musk then it’s not like the real Elon Musk could do anything about it, same thing here.
So is there anything I can do about it?
Not really, no :(
Always check the email address of the sender, especially if an email looks a bit strange.
You might as well hit the ‘spam’ button as it will get the email address shut down quicker and help the email companies anti-spam bots to recognise similar nonsense in future - but other stuff will likely still get through.
What about Facebook Messenger and other social media sites?
If you get spam from a friend via a social media site then it could be
a) A fake account using their name and possibly photos - report to Facebook
b) They are actually been ‘hacked’ right now - report to Facebook and let your friend know by another means.
Passwords people!!!
And time for my daily rant about USING A GOOD PASSWORD yourself and don’t use the same password everywhere. (TODO - advice on that).
Long story short - the vast majority of ‘hacks’ are because people use the same password everywhere. When you sign up to some two bit site that later gets hacked they now have your email/password and it’s not a big step to then try that same email/password all over the place
“Oh but I am clever and change the i’s to 1 on some sites”… right, they will never catch onto that…
Use very different, strong passwords for the important things. If you have too, write them down in an address book (obviously a password manager is better) - the risk of getting hacked is not from some cat burglar pinching your address book - it’s from some tweens out of China running software.
Check https://haveibeenpwned.com/ and sign up to alerts or even better if you use Google Chrome do the security scan that will tell you if you are using any passwords that were also used on hacked sites.